No Bugs Found in Dashlane SaaS


Dashlane
Dashlane is a robust, user-friendly platform designed to secure and simplify digital life. It masterfully combines critical online security tools with a range of convenience-focused features.
This application intuitively manages passwords, secures personal data, and streamlines online transactions. Its digital wallet feature also allows effortless auto-filling of online forms, which is both convenient and time-saving.
As the QAwerk team, we conducted a comprehensive Bug Crawl on Dashlane and found no issues affecting its performance and user experience. Our testing confirmed the platform’s reliability, data integrity, and efficiency in various scenarios.



No bugs found when detecting breached emails and providing recommendations
- The user has at least one monitored email added.
- External service is available for checking breaches.
- Add an email known to be leaked in a past breach.
- Verify if Dashlane detects compromised email.
- Check if relevant recommendations appear for securing the account.
- Remove the email and add it again to check if detection remains consistent.
- Attempt to add the same email multiple times and verify if duplicates are handled correctly.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
Dashlane detects breached emails and provides appropriate recommendations.
Duplicate entries are prevented.
Bug not found.
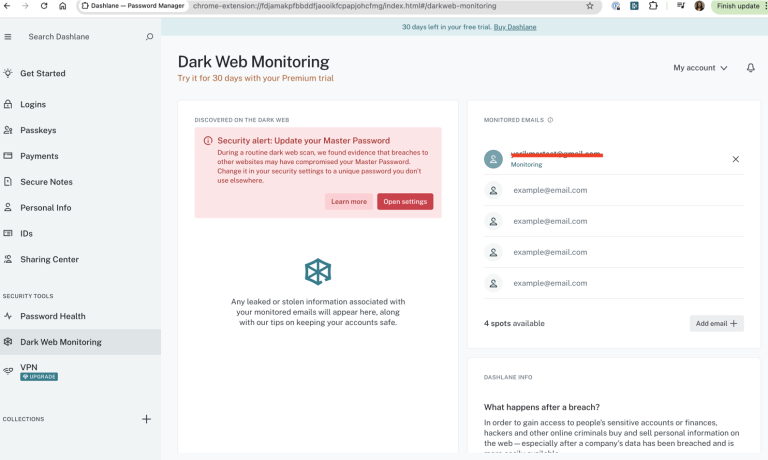
Dashlane detects breached emails and provides appropriate recommendations. Duplicate entries are prevented.
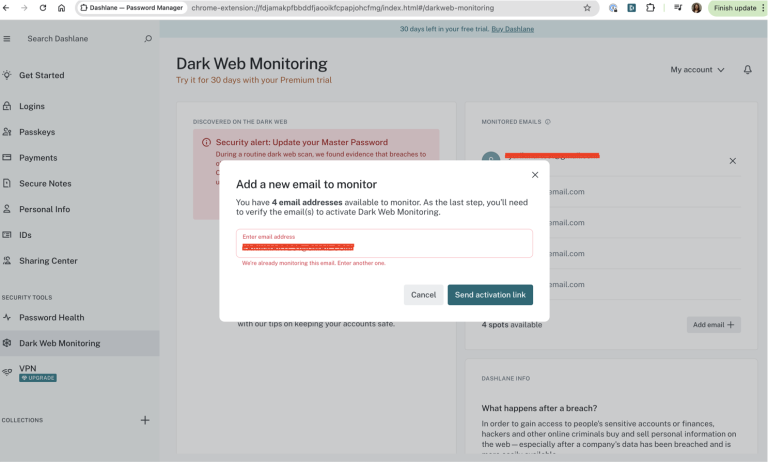
The user is logged in and has no monitored emails added.
- Add emails one by one until the system reaches the limit.
- Attempt to add one more email beyond the limit.
- Observe system response.
- Check if already monitored emails can be removed and replaced smoothly.
- Try adding the same email under different capitalization formats (e.g., TEST@EMAIL.COM vs. test@email.com) and verify uniqueness constraints.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
The system enforces the maximum limit.
Duplicate email variations are prevented.
Overflow is handled properly.
Bug not found.
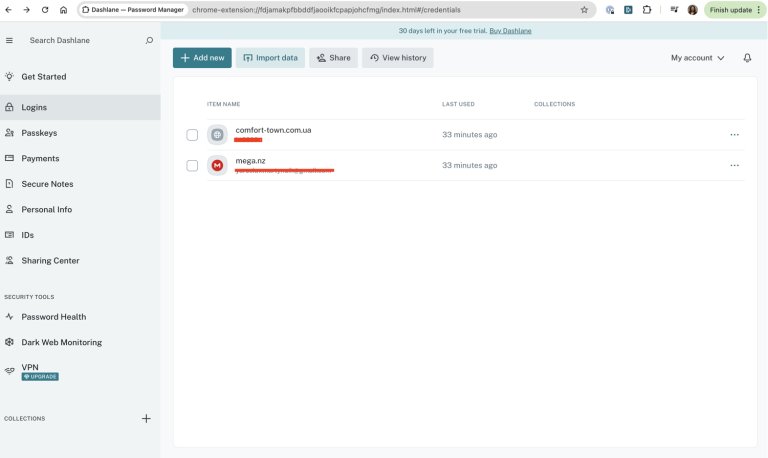
No bugs found when verifying persistence of collections and stored items
The user is logged in and has at least one collection created.
- Create a new collection and add multiple test items.
- Log out and log back in.
- Verify that the created collection and stored items are still present.
- Refresh the page while editing a collection and confirm data consistency.
- Delete a collection, log out, and check if deletion remains effective after re-login.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
Data persists correctly after logout/login and refresh actions.
Deletions remain effective.
Bug not found.
No bugs found when attempting to add payment method
The user is logged in on the platform.
- Navigate to the Payments setup page.
- Click the “Add new” button.
- Fill in all input fields.
- Click the “Save” button.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
The payment method is successfully created.
Bug not found.
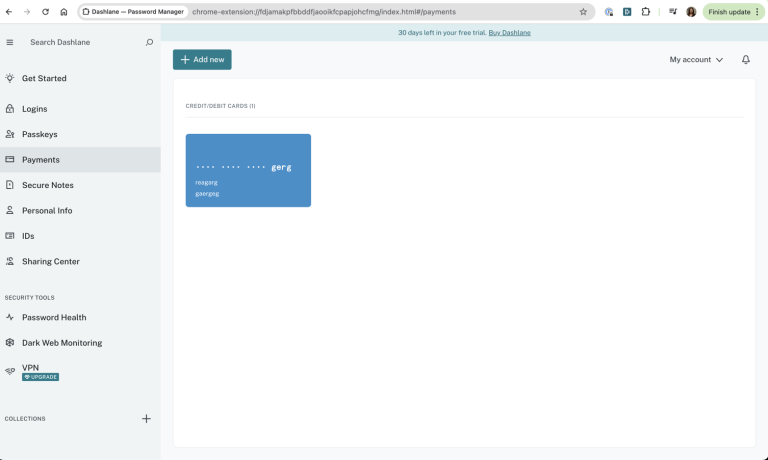
The payment method is successfully created.
The user has stored at least five login credentials in Dashlane.
- Add five strong, unique passwords and observe the score.
- Change one password to weak and observe the impact on the score.
- Modify all passwords to be identical and check the detection of reuse.
- Delete stored passwords and verify if the score resets correctly.
- Try adding a very long but simple password (e.g., aaaaaaaaaaaaaaaaaaaaa) and check classification.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
Password health score dynamically reflects strength, reuse, and deletion correctly.
Bug not found.
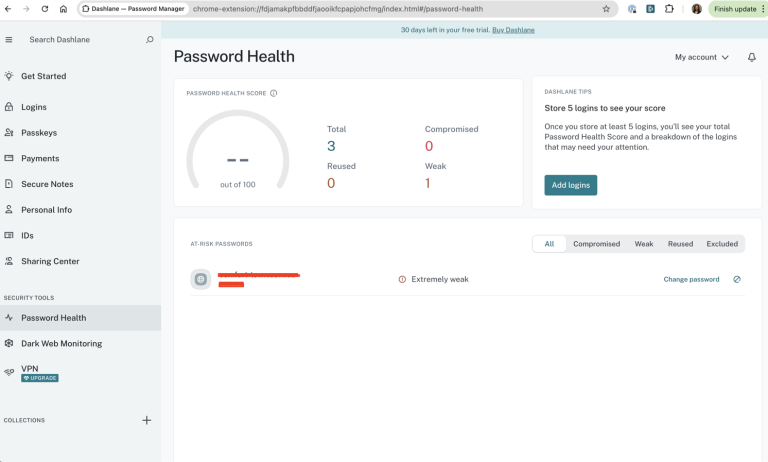
No bugs found when testing secure data export functionality
The user has stored multiple credentials, notes, and monitored emails.
- Navigate to “Settings” → “Export Data.”
- Export data in different formats.
- Select Export to CSV.
- Enter Master Password.
- Open the exported file and verify data accuracy.
- Modify exported data and attempt to re-import it.
- Check if Dashlane prevents importing tampered files.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
Exported data is accurate, and modifications are detected on re-import.
Bug not found.
No bugs found when verifying VPN upgrade flow
The user has a free Dashlane account without VPN enabled.
- Click the “Upgrade” button under VPN.
- Complete upgrade/payment process.
- Verify if the system correctly upgrades the user’s account.
- Attempt to downgrade and confirm refund policies/downgrade options.
- Check if the VPN connection is functional post-upgrade.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
VPN upgrade is processed correctly.
Downgrade/refund policies are properly handled.
Bug not found.
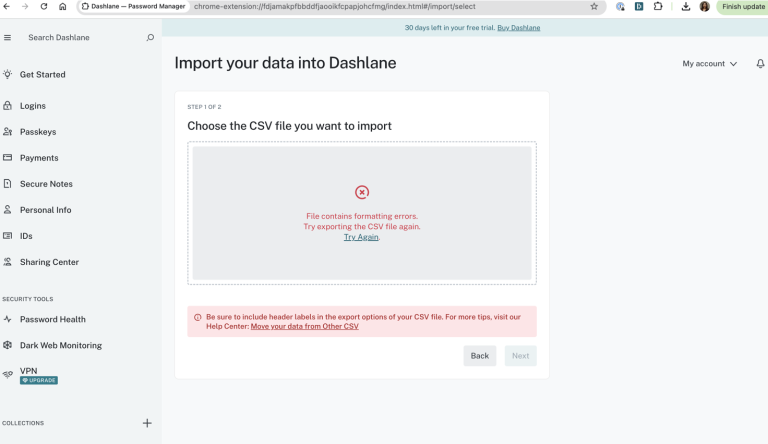
No bugs found when testing import function with malformed credential files
The user has access to the import logins feature.
- Prepare a CSV or JSON file with valid credentials.
- Import file and verify successful parsing.
- Modify the file by introducing syntax errors/malformed data.
- Attempt to re-import and check if the system properly handles errors.
- Observe if misleading data results in incorrect imports (e.g., swapped username/password fields).
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
The system rejects malformed data.
Incorrect logins are prevented from being imported.
Bug not found.
No bugs found when validating session management on multiple devices
The user has access to multiple browsers or devices.
- Log in to Dashlane on Browser A.
- Log in again on Browser B and observe if the first session remains active.
- Manually log out from Browser A and check if Browser B is affected.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
Sessions are handled properly.
Logout behavior is consistent.
Bug not found.
Sessions are handled properly. Logout behavior is consistent.
The user has access to the Dark Web Monitoring feature.
- Rapidly add/remove multiple emails in quick succession.
- Check if the UI updates correctly without delay.
- Observe if API requests fail or rate-limiting mechanisms trigger.
- Verify that the removed emails do not appear after refreshing.
- Attempt to re-add a previously deleted email and check for inconsistencies.
Chrome 131.0.6778.264
Safari 18.1.1
Firefox 130.0.1
The system handles rapid modifications efficiently.
Inconsistencies are prevented.
Bug not found.
I tested Dashlane's security, performance, usability, and load handling under various conditions. The system performed well in most cases, but optimizing mass operations and UI update speed during rapid modifications would make the experience even smoother.

No Bugs Found!
 We tried to find bugs in this product but failed to spot any. While we still believe no software is 100% free of bugs, this app contains no critical or apparent defects that could negatively impact the user experience.
We tried to find bugs in this product but failed to spot any. While we still believe no software is 100% free of bugs, this app contains no critical or apparent defects that could negatively impact the user experience.